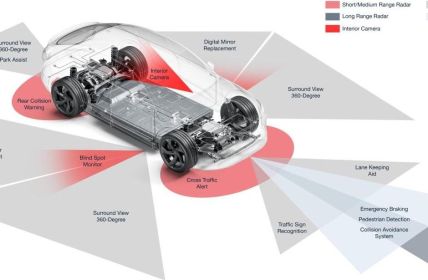
The global use of the Internet of Things in the industrial sector, or IIoT for short, is growing rapidly. Many industrial companies in the field of manufacturing or processing products are planning to invest in IoT devices.
Table of Contents: What awaits you in this article
Reasons for Extensive IIoT Networks
Therefore, it will not be long before there are very complex IIoT networks. The more this technology advances, the greater the risk of cyberattacks. For this reason, it is important to ensure a high level of security from the outset. Basically, there are four key steps to achieve a high level of protection for IIoT networks against cyberattacks.
Use network monitoring
The first step is to get a comprehensive overview of all IoT devices that are integrated into a network. The backend of IIoT networks can be used to determine exactly what tasks each IoT device is performing. The connections and communication options of the individual components can also be seen there.
To prevent cyberattacks, it is particularly important to find out which components communicate with the outside world. Any component that sends data to servers or other devices that are not inside the network are a potential threat. These must be given special protection. Once an overview has been created in this way, a plan for security should be put in place.
Set up protection against DDoS attacks
A distributed denial of service or DDoS attack poses a serious threat to the enterprise. The perpetrators are constantly changing and optimizing their approaches. That’s why traditional defenses don’t work in every case. While they provide good basic protection against cyberattacks, they never fully protect.
The real problem is that not all components in IIoT networks are secured in the same way. This allows attackers to exploit the weakest link in the chain. Computer and storage device manufacturers are particularly popular targets. Netscout’s Threat Intelligence Report even reports that attacks from companies in this industry increased by 263 percent in 2021.
Protect IIoT networks with firewalls
The first step in this direction should be segmentation. IoT devices that do not necessarily need to communicate with all other devices should be treated separately. In addition, it should be prevented that not every component can establish a connection to the outside world. This is difficult in that most IoT devices are equipped with numerous communication standards.
Therefore, a firewall should definitely be set up. In this, ports are released through which internal communication is enabled. Ideally, a separate firewall is configured for each individual IoT component. This can be very costly in complex IIoT networks. But such a measure offers the best protection against a cyberattack.
Prevent cyberattacks with encryption
Data exchange in IIoT networks should definitely be done with end-to-end encryption. In that case, the data can only be made usable with the appropriate key. Powerful tools are already available for this purpose. In addition, important functions should be secured with passwords.
Secure passwords are best created with random generators. In addition, password rotation should be integrated into the system. It may sound a bit elaborate to secure the IoT devices in IIoT networks with passwords and encryption algorithms, but this procedure offers a high level of protection against cyber attacks.