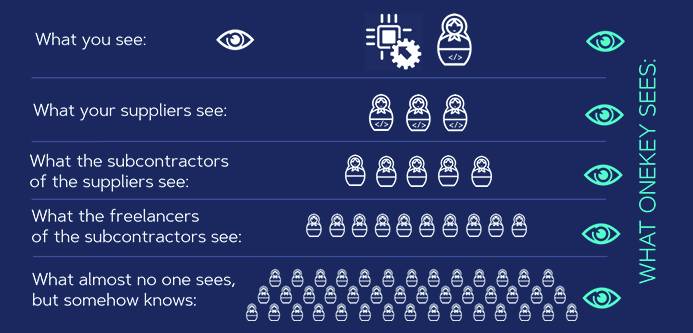
ONEKEY GmbH has recognized the need for transparency as the basis for security in the software sector. This is made possible with the ONEKEY software platform, as it is able to create a bill of materials for software (Software Bill of Materials, SBOM). Digitization is progressing and we are already surrounded by a multitude of intelligent devices. According to forecasts, 40 billion devices will be networked by 2025. The concentrated “intelligence” is not problematic, but how it is used. Security gaps are breeding grounds for crime and reports of hacked systems are piling up.
Table of Contents: What awaits you in this article
SBOM as the basis for security in the company
In order to identify possible points of attack in the software used and to create security, a company must know exactly which components its software consists of. This is mapped by the SBOM. This lists exactly the integrated components. If a component has a vulnerability, this can weaken an entire system in the event of an attack or even lay a company down in the end. “You must know the enemy in order to defeat him”, said already 500 BC. Christ the philosopher Sunzi.
That still applies today. If I know the error thanks to transparency, I can eliminate it and protect myself. Last year ended with an IT crisis. The Log4j vulnerability made authorities and companies vulnerable worldwide – mainly because the SBOM was often missing and it was not clear whether you were affected or not. The Federal Office for Information Security (BSI) issued a red level cyber security warning.
Global threat of vulnerability
Log4j has been widely used for logging in Java applications. On December 10, 2021, the vulnerability (CVE-2021-44228) was discovered on the servers of the online game “Minecraft”. Every new vulnerability is made public after 90 days and registered in the worldwide CVE databases (Common Vulnerabilities & Exposures). This period is used by the manufacturer to carry out mitigating updates.
Without this measure, any hacker could exploit the vulnerability before a user realizes they have a vulnerable point. It is of little use to a company if it knows that there is a vulnerability in component X if it cannot identify which software has this component. The SBOM is not available for every software in Germany, and the growing mass of technology does not make it easier to get an overview.
The parts list is already mandatory in the USA, but it is on the way in the EU. In 2023, the Cyber Resilience Act (CRA) will oblige manufacturers of technical devices to continuously monitor security. But what can a company do that currently lacks the SBOM for its software and thus security? ONEKEY GmbH provides the solution here.
ONEKEY: Provides solution and subsequently creates SBOM
ONEKEY has developed a technology that is able to read the binary code of a software. So far, hardly any conclusions were possible on this basis – without the source code. The focus of the security specialist is on Industrial IoT and operating technology (OT). The ONEKEY software platform decrypts the binary code of software, reveals all components and subsequently creates the SBOM.
After the software component analysis, from which the SBOM emerges, a security analysis is carried out. Are all components secure or are there any vulnerabilities? The customer receives complete transparency about his software and can protect himself. In a third step, the ONEKEY technology checks whether IT compliance is being observed. The corresponding standards, such as IEC62443, ISO, DIN, ETSI and other standards, are stored in the platform. Compliance violations are identified and automatically reported to the customer.
Focus on Industrial IoT & Operational Technology (OT)
The private person is not primarily interested in whether something is safe. ONEKEY is clearly addressed to industries. This includes manufacturers and operators of smart devices, e.g. from the automotive, manufacturing, medical devices, telecommunications and critical infrastructure such as energy / water supply sectors.
Hacker attacks are increasing. As a result, more and more industrial companies are realizing that their existing technology is not secure and urgently needs an analysis. In addition, there are more and more legally prescribed specific standards for the individual areas. If a manufacturer does not produce safe products, sooner or later they will have a problem with their core business.
ONEKEY offers individual service
ONEKEY has the vision of becoming an essential factor for transparency and security in the industrial production and product environment. Depending on their technical level, customers have two options. Companies with their own IoT security experts can run the ONEKEY platform easily and inexpensively as an annual subscription, without the need for additional training and advice. For companies that have little expertise in the field of IoT security, a hybrid offer consisting of an automatic platform with additional expert advice is available.
In that case, ONEKEY does the work for the customer. For special cases, e.g. if the devices are 20 years old and cannot be analyzed automatically, the security specialist offers an individual analysis (penetration test) also by experienced experts.